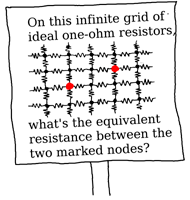
Operation Mindfuck Vol. 4
bleeptrack & blinry
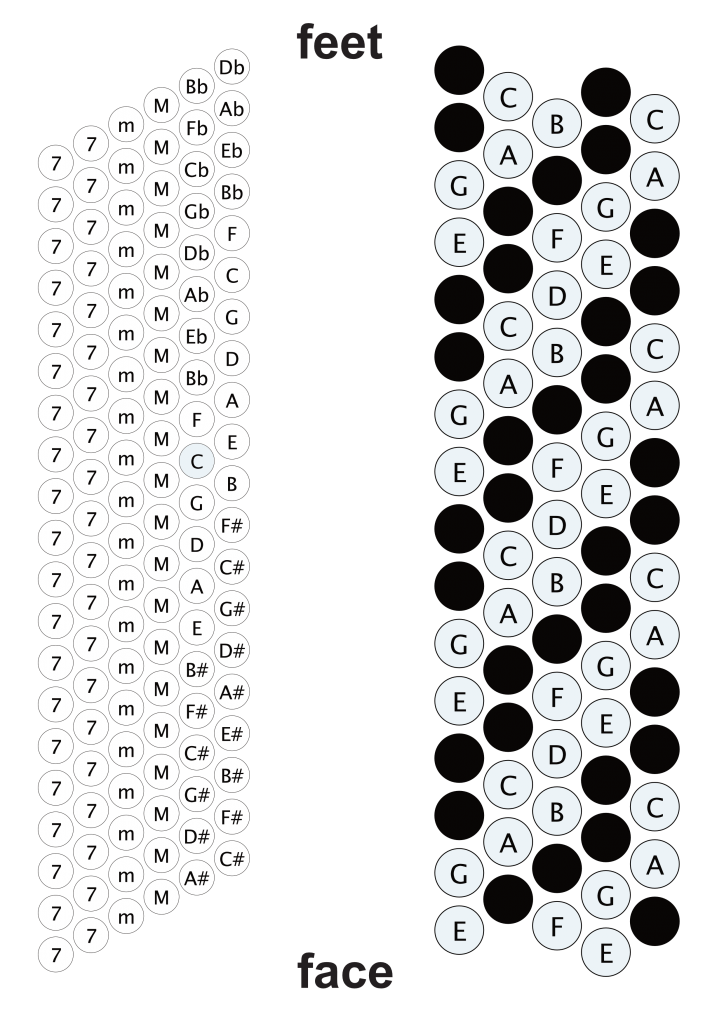
Isomorphic keyboard layouts

"Dodeka"

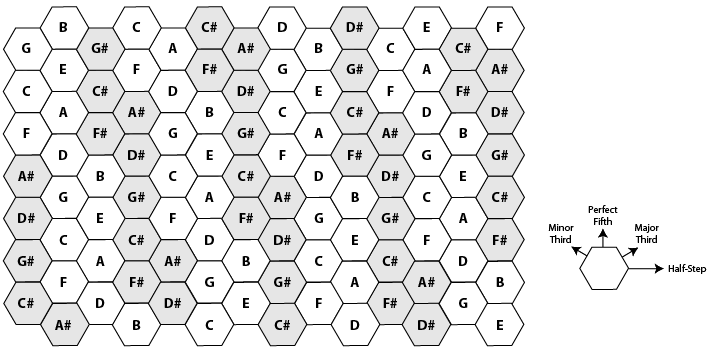
Harmonic table layout
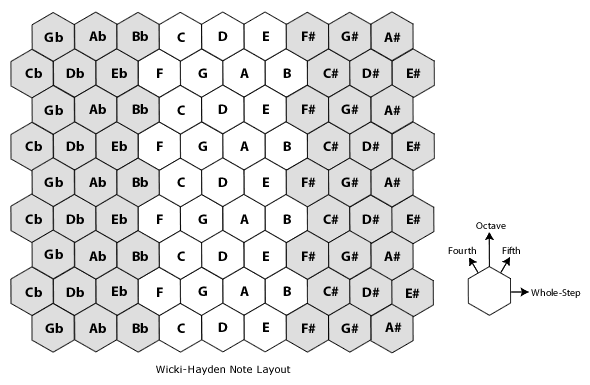
Wicki-Hayden layout
"Jammer keyboard"


Truchet Tiles
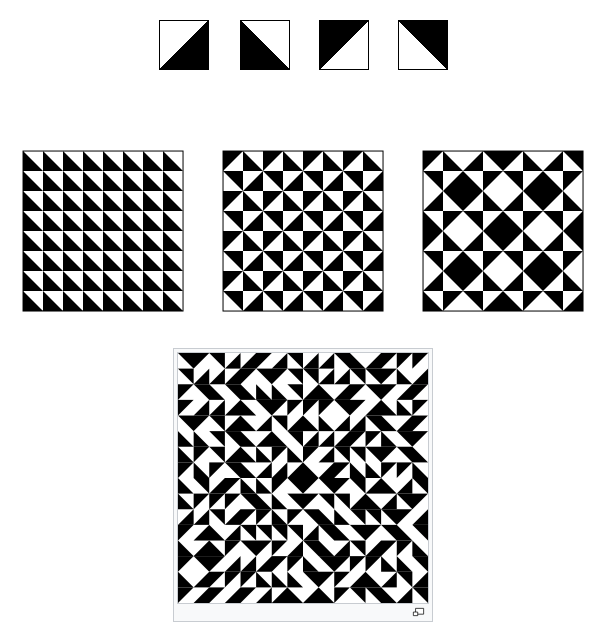
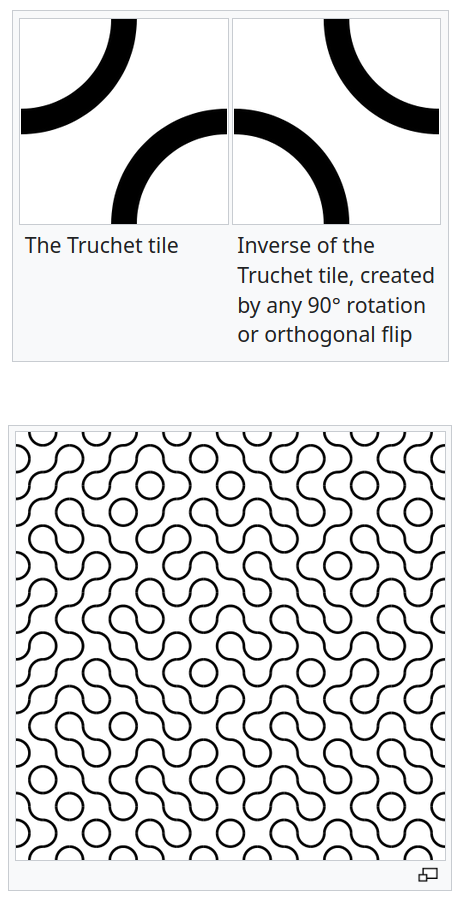
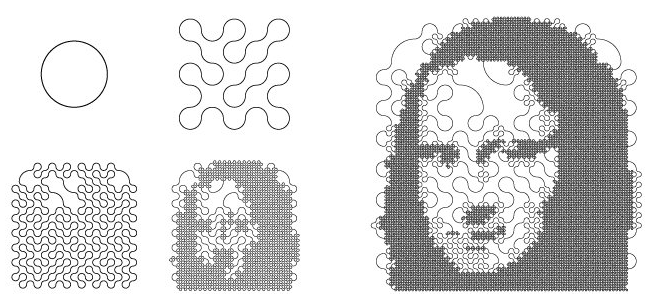
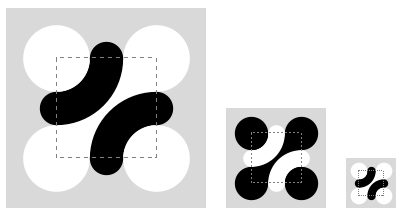
by Christopher Carlson
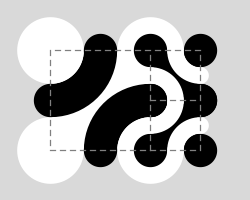
by Christopher Carlson
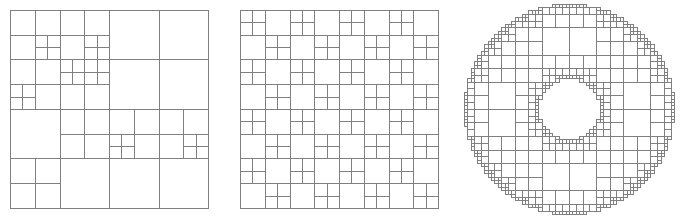
by Christopher Carlson

by Christopher Carlson
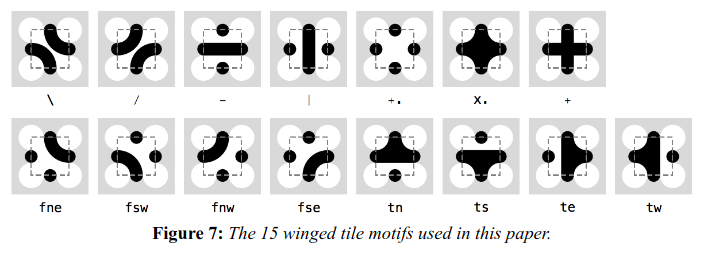
by Christopher Carlson

by Christopher Carlson
What even is art?
"Comedian" (Cattelan, 2019)

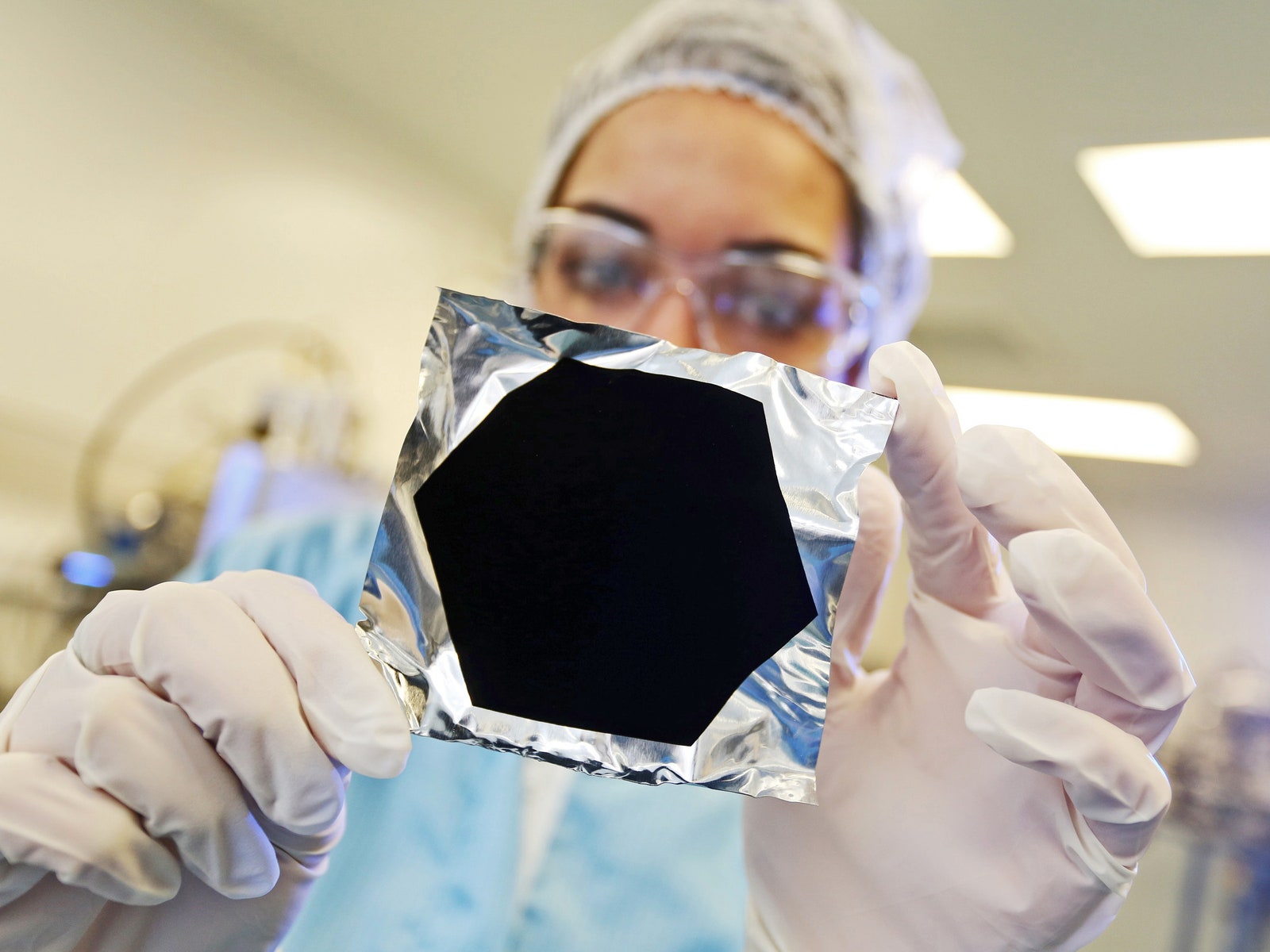
"Descent into Limbo" (Kapoor, 1992)


"Love is in the Bin" (Banksy, 2018)

"Fettecke" (Beuys, 1982)

"Reste einer staatlich zerstörten Fettecke" (2014)

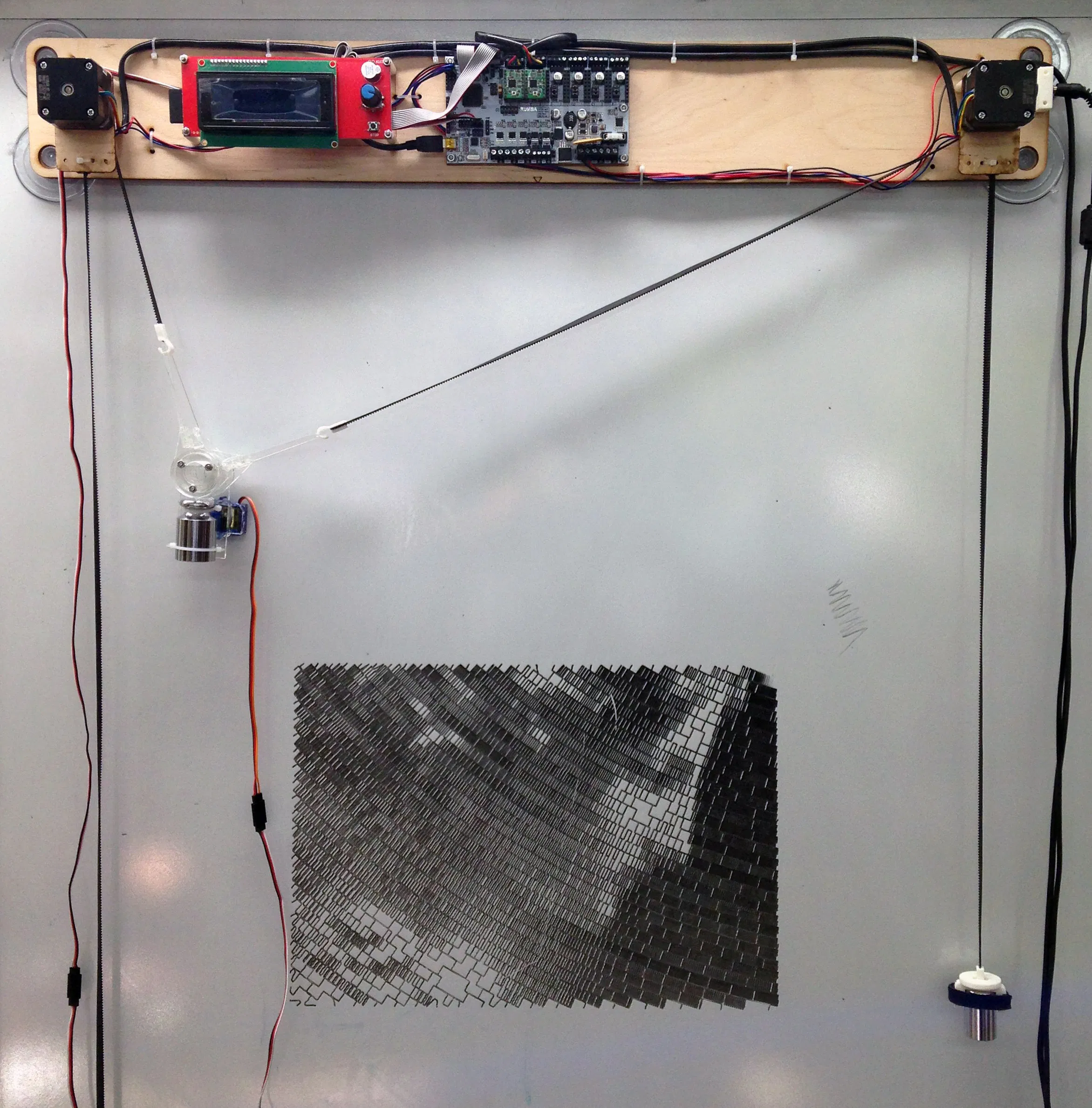
Pen Plotter
April fools' RFCs
RFC 1149: IP over Avian Carriers
The carriers have an intrinsic collision avoidance system, which
increases availability.
Multiple types of service can be provided with a prioritized pecking
order.
With time, the carriers are self-regenerating.
An additional property is built-in worm detection and eradication.
Implementation:
Script started on Sat Apr 28 11:24:09 2001
$ /sbin/ifconfig tun0
tun0 Link encap:Point-to-Point Protocol
inet addr:10.0.3.2 P-t-P:10.0.3.1 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:150 Metric:1
RX packets:1 errors:0 dropped:0 overruns:0 frame:0
TX packets:2 errors:0 dropped:0 overruns:0 carrier:0
collisions:0
RX bytes:88 (88.0 b) TX bytes:168 (168.0 b)
$ ping -c 9 -i 900 10.0.3.1
PING 10.0.3.1 (10.0.3.1): 56 data bytes
64 bytes from 10.0.3.1: icmp_seq=0 ttl=255 time=6165731.1 ms
64 bytes from 10.0.3.1: icmp_seq=4 ttl=255 time=3211900.8 ms
64 bytes from 10.0.3.1: icmp_seq=2 ttl=255 time=5124922.8 ms
64 bytes from 10.0.3.1: icmp_seq=1 ttl=255 time=6388671.9 ms
--- 10.0.3.1 ping statistics ---
9 packets transmitted, 4 packets received, 55% packet loss
round-trip min/avg/max = 3211900.8/5222806.6/6388671.9 ms
Script done on Sat Apr 28 14:14:28 2001
RFC 6592: The Null Packet
Null Packets are neither sent nor acknowledged when not received.
2. The Null Packet
The Null Packet is a zero-dimensional packet. The Null Packet exists
since it is non-self-contradictorily definable.
2.1. Formal Definition
[This section is intentionally left blank, see also Section 0 of
[NULL].]
6.1. Normative References
[NULL] "".
4.2. The Null Packet is Good
The Null Packet cannot have the Evil Bit ("E") [RFC3514] set, by
definition (see Section 2.1). Consequently, it is rather clear and
undeniable that the Null Packet is harmless, having no evil intent.
RFC 3514: The Evil Bit
The high-order bit of the IP fragment offset field is the only unused
bit in the IP header.
The bit field is laid out as follows:
0
+-+
|E|
+-+
Currently-assigned values are defined as follows:
0x0 If the bit is set to 0, the packet has no evil intent. Hosts,
network elements, etc., SHOULD assume that the packet is
harmless, and SHOULD NOT take any defensive measures.
0x1 If the bit is set to 1, the packet has evil intent. Secure
systems SHOULD try to defend themselves against such packets.
Insecure systems MAY chose to crash, be penetrated, etc.
- RFC 2324: Hyper Text Coffee Pot Control Protocol
- RFC 5841: TCP Option to Denote Packet Mood
- RFC 7511: Scenic Routing for IPv6
Unrealistic Expectations
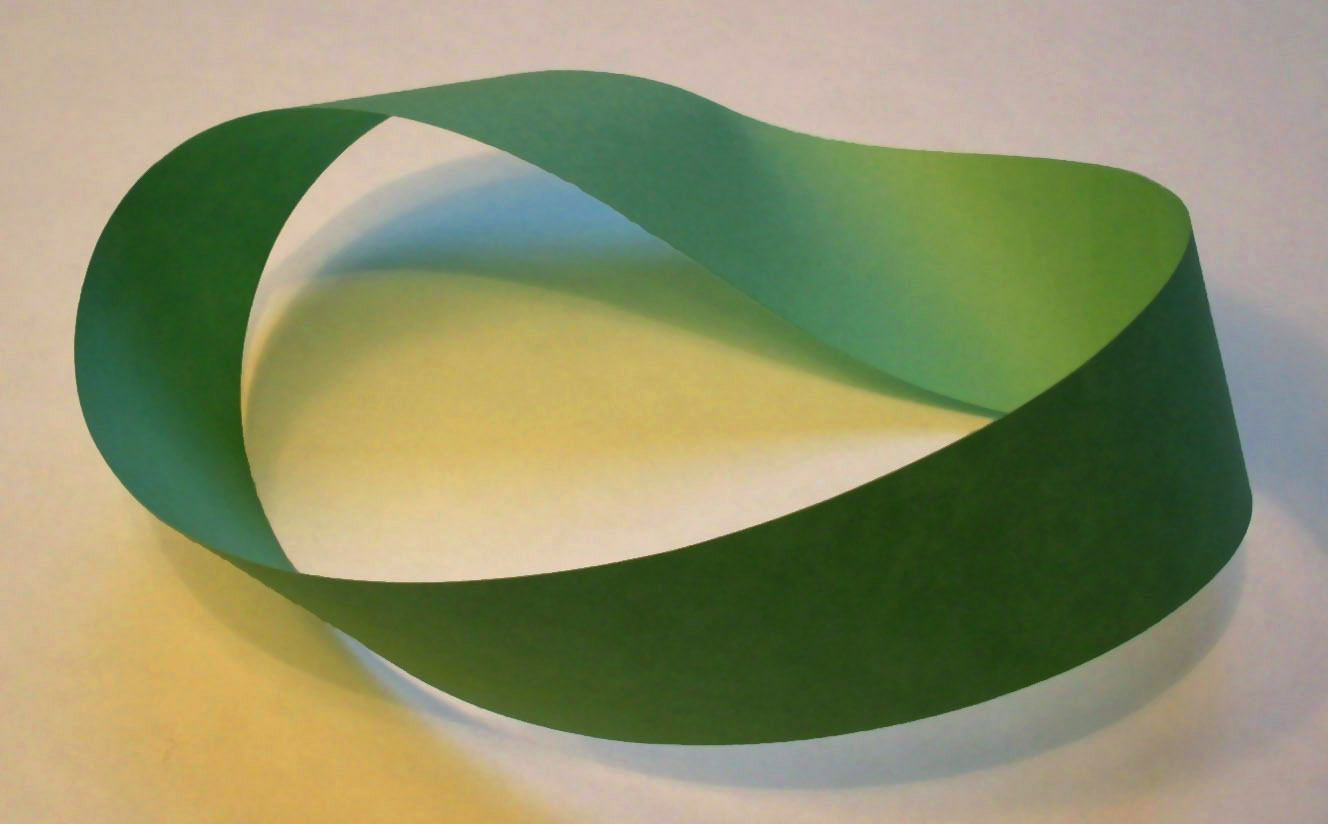
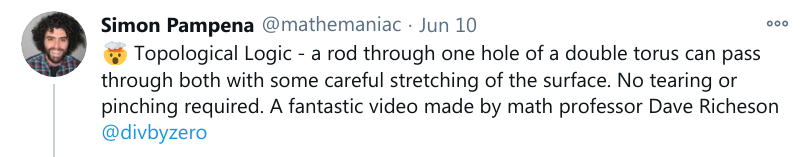
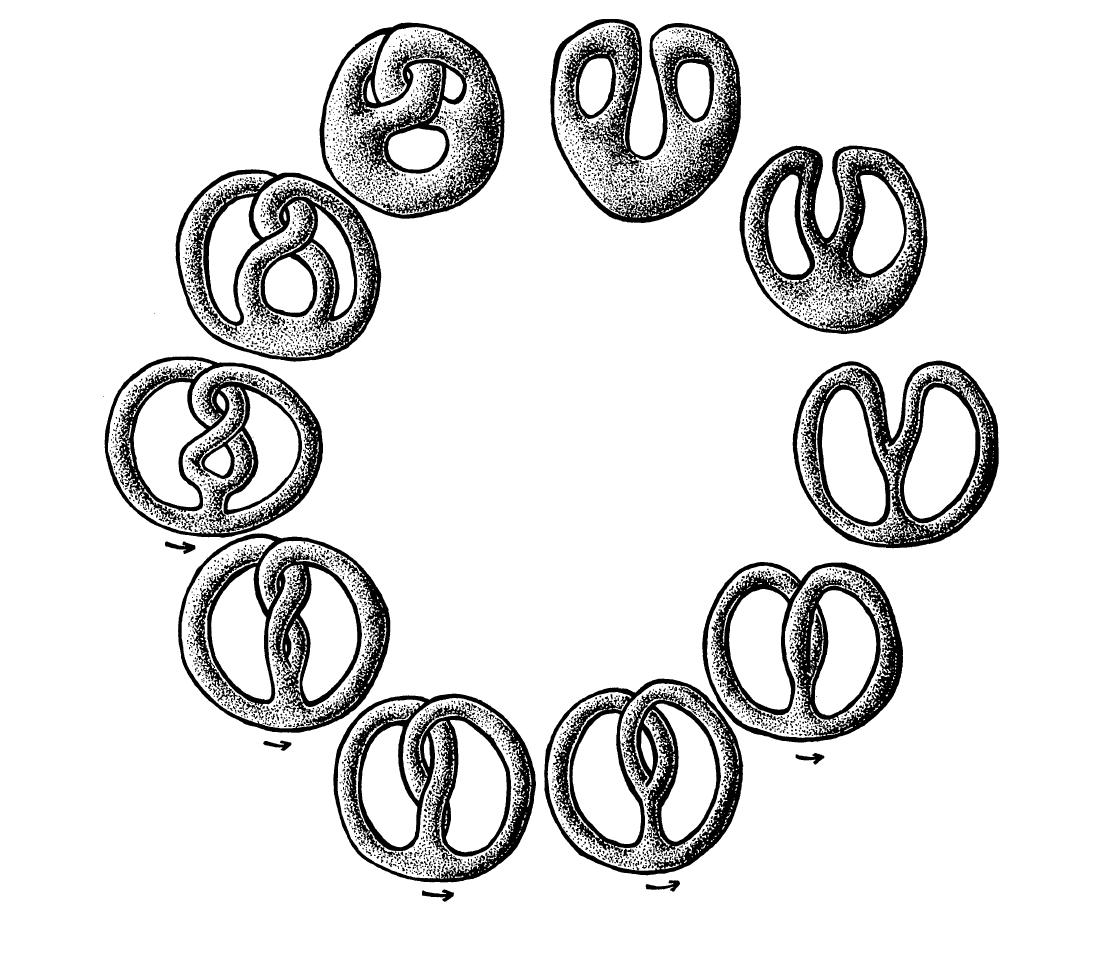
Fun with topology

PCB Art
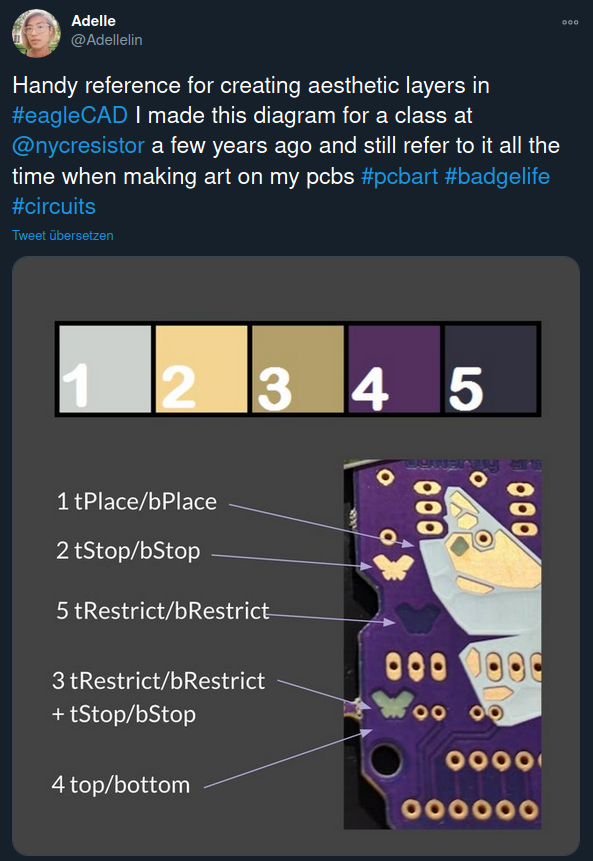
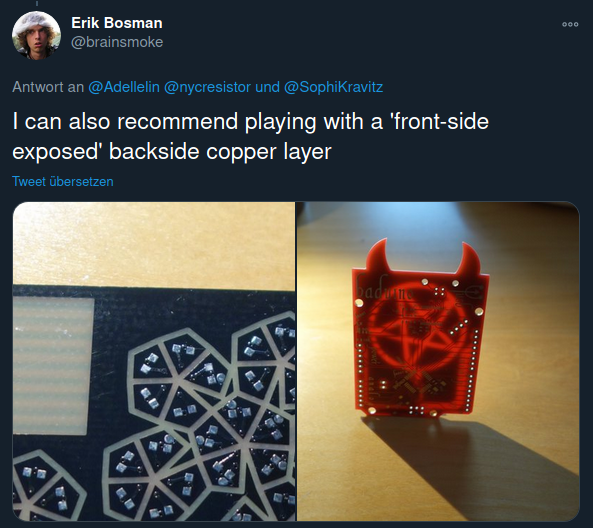
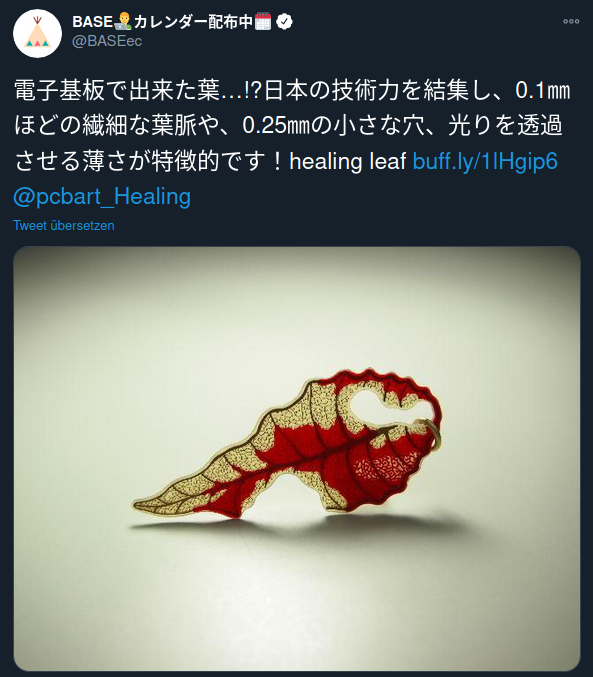
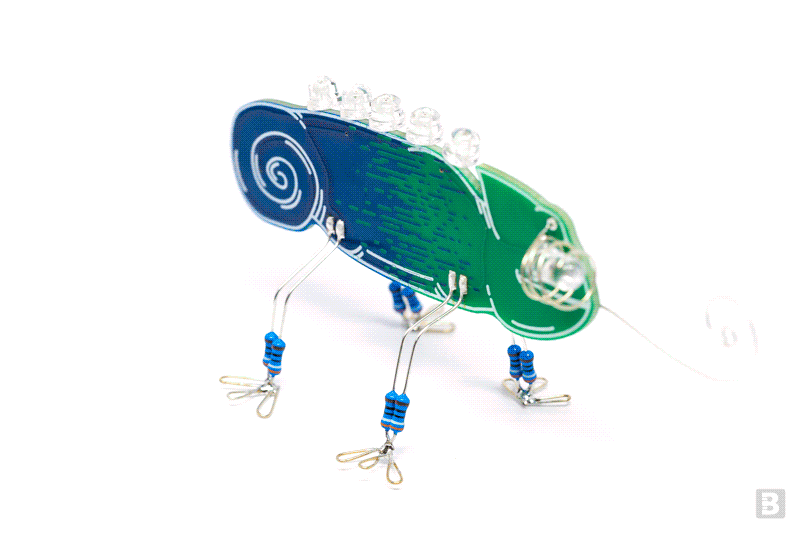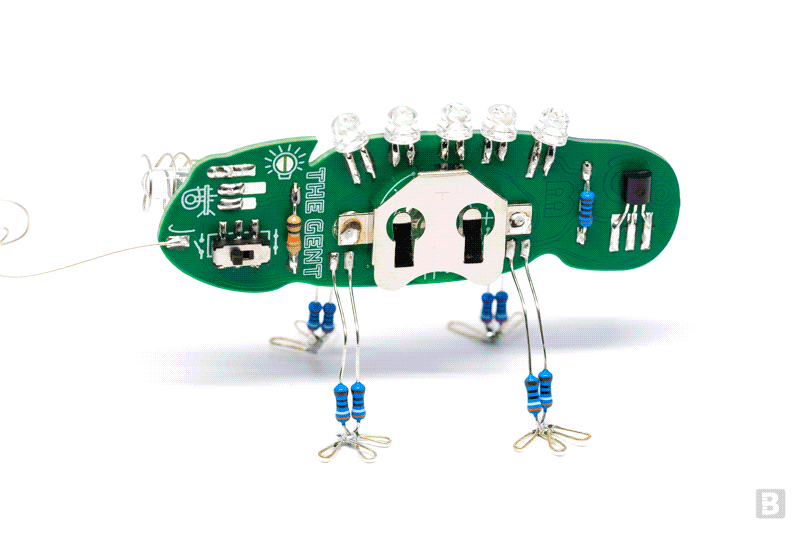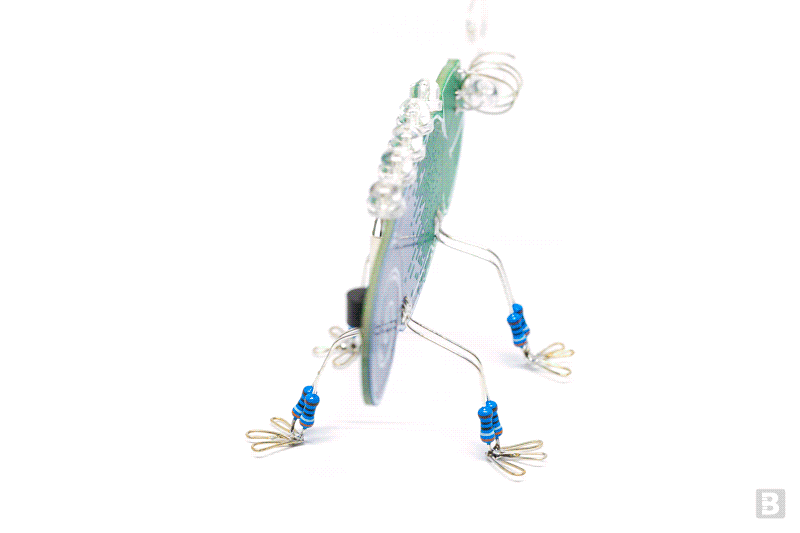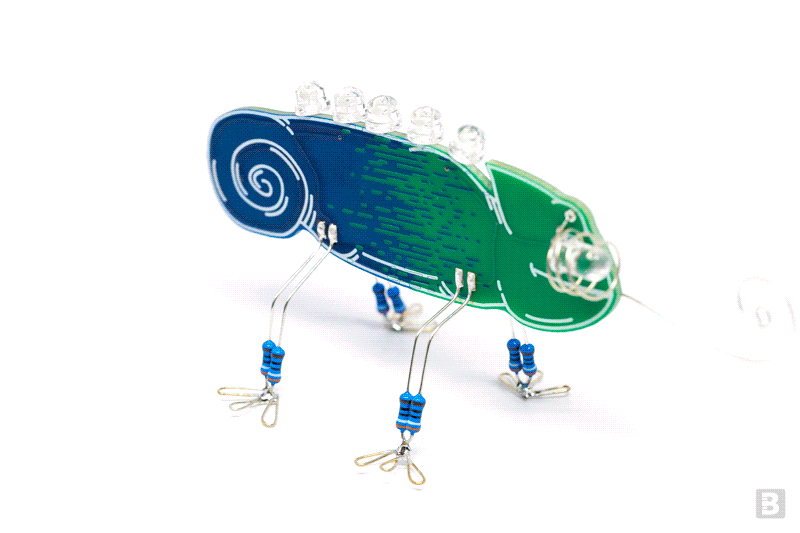
by boldport

Rabbit holes!
- mechanical keyboards
- skincare addiction
- amateur astronomy
- baking your own bread
- ultralight backpacking
- sharpening knives with a wet stone
Thanks!

Slides: morr.cc/operation-mindfuck-4/